A single change to a network device can have far-reaching effects on your business. It can create security holes for cybercriminals, impact your regulatory audit, and even cause costly outages that can bring your business to a standstill – as we have recently seen in the news!
This technical webinar will walk you through a variety of scenarios that can cause device misconfigurations, including a basic device change, business application connectivity changes, and data center migrations. It will provide both best practices and demonstrate specific techniques to help you understand and avoid misconfigurations and ultimately prevent damage to your business, including how to:

Firewall rule automation & change management explained
In today’s IT environment, the only constant is change. Not only is change rampant, but it often occurs at breakneck speed. Rapid business growth from mergers and acquisitions, development of new and de-commissioning of old applications, new users, micro-segmentation, cloud migrations and more make for a dynamic environment that poses new security challenges all the time.
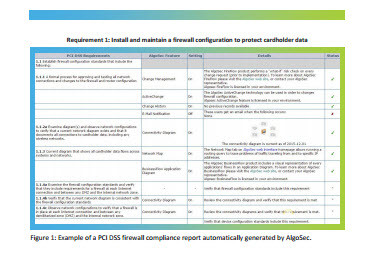
The Business Case for Network Security Policy Management
This paper will examine five business challenges that many organizations face and present a savings calculation and business justification based on operational efficiency that can be used to facilitate budget approval.

Security Policy Management Across the Next Generation Data Center
This paper examines the new realities facing today’s security, networking and application teams, the challenges of managing the security policy in an environment of constant change and complexity, and the solutions that can help manage security at the speed of business.
The Security Policy Management Maturity Model
Through a detailed analysis of the security policy management maturity model, this webinar helps organizations assess their current environment and provides a roadmap for reducing complexity, ensuring application connectivity, and improving their overall security posture.