Categories
Findings from Our Recent Security Management Survey
Over the last weeks, we have surveyed over 100 security professionals (none of which were AlgoSec customers by the way) to try and gain some insight on what organizations are struggling with when it comes to network security policy management.
As is often the case with survey data, most results were in line with what we are seeing in the field every day working with our customers and partners. But the survey did uncover some surprising results and good insight.
As far as demographics go, most respondents (50.9%) stated they have between 10-49 security gateways in total (these include firewalls, IPS/IDS, content filtering, anti-virus etc.) but there was good representation for both smaller organizations (27.7% have 1-10 gateways) and enterprises (17.5% have more than 50 gateways).
Here are some key findings from the survey:
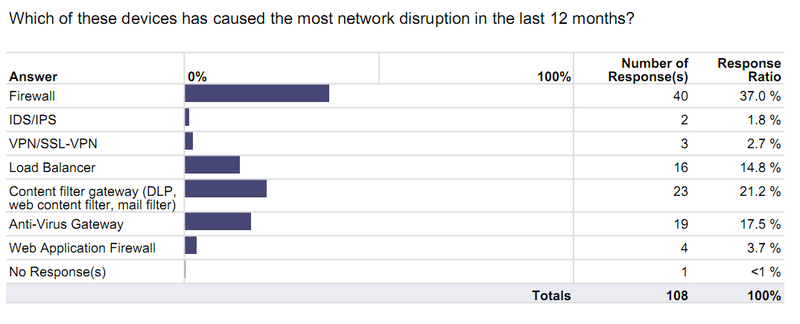
- All security gateways cause network outages! – When asked which security gateways have caused the most outages in the last 12 months, every technology had representation. Firewalls caused the most outages, followed by Content Filtering gateways and Anti-Virus gateways. IPS/IDS caused the least amount of outages, but this is most probably due to the fact that it is only deployed by 41.6% of respondents, and it is safe to assume that many deploy it in “detection only” mode.
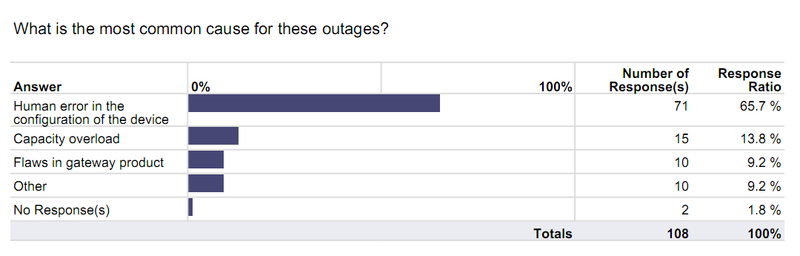
- Human error is the most common reason for these outages – We were quite surprised that as many as 65.7% of respondents cited human error as the primary reason for these outages as opposed to only 13.8% citing capacity overload. A logical conclusion would be that organizations should look beyond investing in “throughput” out of fear for network disruptions, and consider investing in security management tools which can minimize human error – a greater cause of network disruptions.
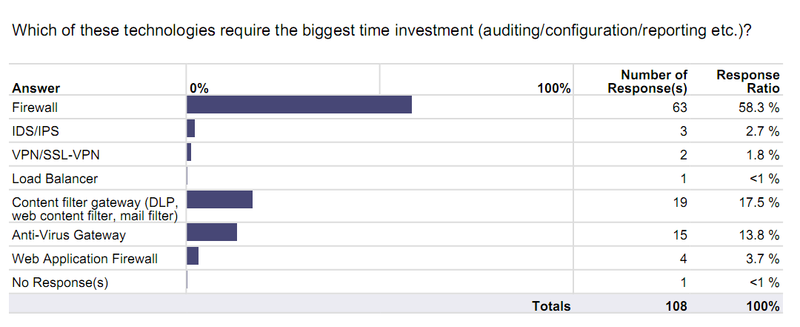
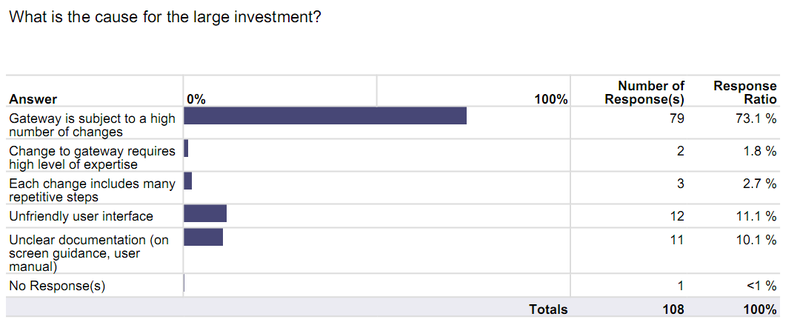
- Security Change Management is a big challenge – Firewalls take up the most management overhead (hardly a surprise for us of course), with 73.1%(!) citing a high number of changes as the main cause for the time investment.
If there is one key takeaway from the survey, I think it is that organizations must be aware of the impact of security configuration errors and take steps to minimize them. Here are some points to consider:
- Factor-in ease of use when selecting security products – Which of the two do you prefer – a great security product that is misconfigured or a good security product that is well configured? Make sure to give ample weight to ease of management and configuration when selecting security products.
- Continuous training – it’s not enough to train your security and operations team when you first deploy a new technology. Make sure you allocate the time and budget to ensure security staff is up to speed with latest know-how.
- Automate as much possible – automation is not only about operational efficiency, it’s also about reducing errors. Invest in tools that can help you automate security configuration and/or discover configuration errors.
- Review change management processes – change management is often the weakest link when it comes to security management. Make sure you have the processes and tools to ensure changes do not introduce new problems.
Subscribe to Blog
Receive notifications of new posts by email.

