Categories
Would You Like Your Data Back? It Will Only Cost $1,000 – Love, Ransomware
Happy New Year! You wake up to find that your files have been encrypted by someone else. And now the only thing that is readable is an html file, informing you that for a fixed price you “may” receive the magic key to unencrypt those files. This is Ransomware – where someone encrypts your files and then leave an html message – a ransom note – for the owner. Below is a description of the process that we created:

The reason for the html file is because it allows the message to be displayed in various ways, to fool the user into thinking that it’s from a legitimate website (such as a local government site):
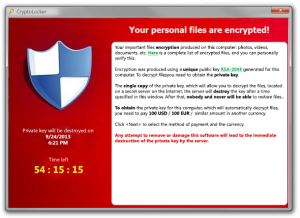
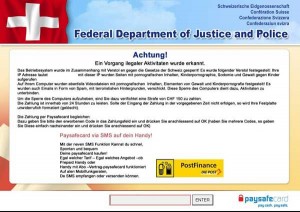

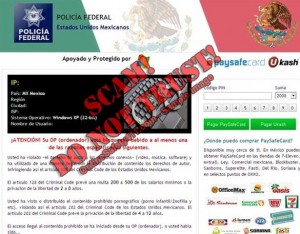
This type of cyber attack is referred to as a “data hijacking attack”, where the data or files are hijacked for a particular purpose, either monetary or something more sinister. There are many virus versions that fall into this virus classification: CryptoLocker, CryptoWall 1.0, Chimera, TeslaCrypt, etc. to name a few.
These applications/programs are often shared among cyber criminals, so pinpointing a single source is often not possible, especially when they can be rented as a service for others to use for a small fee. With a simple process of infection, encryption and notification these viruses have been extremely successful. One Ransomware virus “CryptoWall 3.0” made over $325,000,000!
There are however prevention methods that can greatly reduce the impact of data hijacking attack:
- Have a Phishing Email Plan – Fake emails (phishing emails) spearhead most cyber-attacks. Ensure you have a mitigation plan, a process, and a communication matrix. The goal of the plan is to enforce the idea of “Don’t Open Suspicious Emails”
- Secure Your Devices – Ensure you have proper security applications like Anti-Malware/Virus, Host Intrusion Prevention, or even White Listing. Having multiple layers of security works well.
- Take Data Offline – Data/files that aren’t constantly used – ex. on a daily basis – should be taken off-line or put on a separate device. By reducing the targets you will minimize the potential impact of an attack.
- Practice Safe Surfing– Web browsing habits do play a vital part in limiting your exposure to these types of attacks. The shadier the site, the more probable you’ll be attacked.
- Give Yourself a Chance – There are programs that can undo the encryption, but they require system configurations like shadow copy or system restore. Enable them now!
- Take Less When Traveling Abroad– Laptops, debit cards, social cards, iPads, iPhones, etc if it is not vital for the trip, leave them at home. Many countries do not have cyber laws.
- Don’t Forget the Fundamentals – Backup, Backup, Backup. Backing up data can ultimately save you. While you will lose some data, you will not lose all of your data, unless you don’t backup.
- Make it Muscle Memory – This is a good habit I learned in the Marines. Muscle memory is the basic premise of repeating an action so many times, that it no longer requires thought. Having constant dialog about the process, the possibilities, the mitigation steps until it’s a reaction and not a thought, will improve your security posture.
Ransomware and data hijacking are a real problem – they have become so successful that organized crime, nation states and other hostile entities are using them as one of their primary weapons to extort their targets. Following these simple yet effective steps will help arm yourself against them. Unfortunately one of my previous companies didn’t, and it cost them…
While on vacation I received a call from my security analyst asking me, somewhat innocently, if I knew a way to decrypt files. When I asked why, he told me that a user’s laptop had been impacted by a ransom virus. Not only that, the attack has gone much further than the person’s individual laptop. Since the user had mapped her drives to application servers, ransom virus was able to access and impact any server she was connected to. So all the files on those application servers had also been encrypted by the ransomware! Of course we didn’t have any backups, system restore enabled or shadow copies. The company lost important files and suffered productivity loss and financial loss as a result.
Subscribe to Blog
Receive notifications of new posts by email.

