Authentication
For more details, see Configure user authentication and Integrate ASMS and CyberArk.
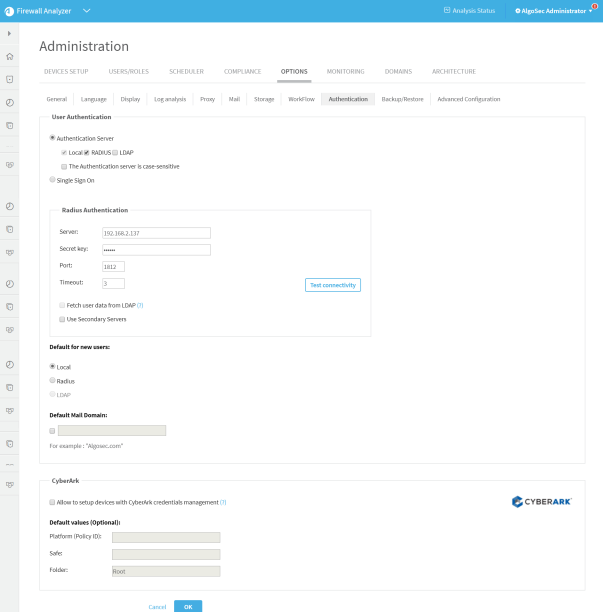
For more details, see Configure user authentication and Integrate ASMS and CyberArk.

Did you find this helpful? ![]() Yes
Yes ![]() No
No
Why wasn't this helpful? (check all that apply)
Thanks for your feedback!
Shoot us an email. This way we can let you know when we've updated the docs.
Thanks for taking the time to give us some feedback.