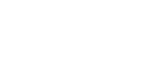Risks page
The Risks page summarizes all risk analysis findings. For example:
This page includes the following data:
-
The device's security rating, which indicates the device's degree of compliance with security standards. A security rating of 100% indicates full compliance.
-
The total number of risks in each severity category, not counting duplicates.
-
A graph displaying the security rating trend.
- A list of all the device's risks, in decreasing order of severity. The New label indicates risks that were not present in the previous report.
Drill down to specific rules and groups
Use links to drill down to more details for each threat, specific rules that require changes, and so on.
Do the following:
-
Click on a risk.
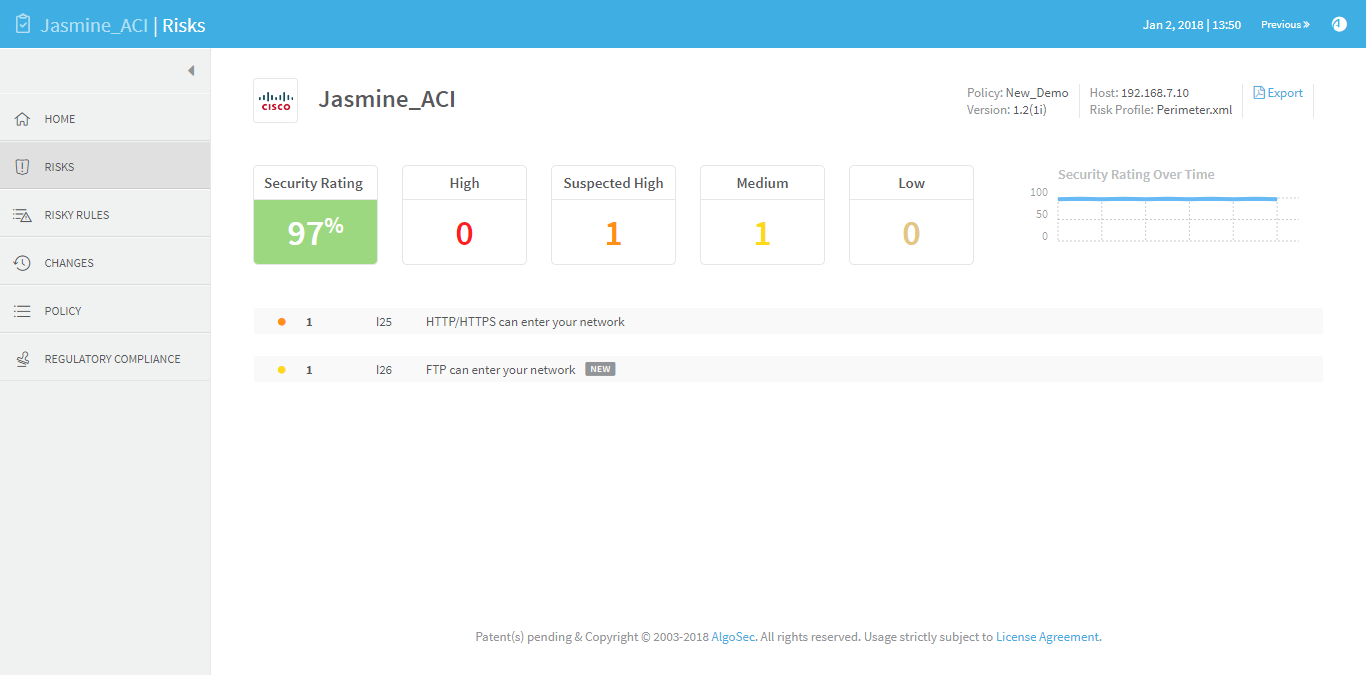
The Risk Assessment details appear, displaying the findings and the recommended remedy. The risk is presented in a descriptive manner with links to every entity that is associated with the risk.
In the example below, AFA displays the number of internal and external IP addresses that have access/are reachable by the risky service.
-
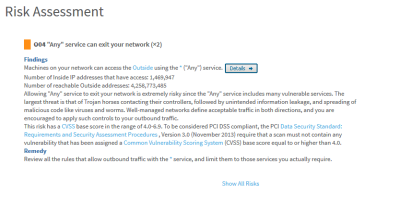
Click the Details button to view the specific rules that allow access to the risky services.
For example:
In the following image, we see that rule 36 looks like an accept rule that allows outbound access:
Allowing any outbound service is not recommended since it may be used by Trojan horses to attack business partners. However, this does not explain why any service is allowed from the outside.
Therefore, we navigate further and click on the group GP_NW_Garden_ICN to examine its definition.
The following image shows that host group GP_NW_Garden_ICN, an EPG, spans the device:
- The purple dot
 indicates that some of its IP addresses are outside of the network. These IP addresses are listed to the right of this icon.
indicates that some of its IP addresses are outside of the network. These IP addresses are listed to the right of this icon. - The blue dot
 shows that other IP addresses are on the inside. These IP addresses are listed to the right of this icon.
shows that other IP addresses are on the inside. These IP addresses are listed to the right of this icon.
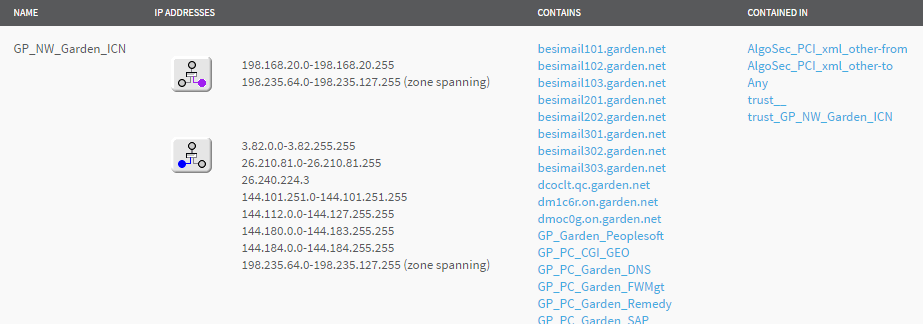
Since the rule that uses this host group allows access to any destination, the outside addresses (198.168….) are allowed to enter the network with any protocol. This is a serious vulnerability.
In this case, the likely culprit is a simply typo: the administrator probably planned to enter "192" (which is an inside address) and mistakenly entered "198".
Note: Similar vulnerabilities exist in all large organizations. Scanners do not find these, and human audits will rarely find them either, as all IP addresses look the same. AFA finds and highlights these vulnerabilities automatically.
Tip: Click on the icons in the IP ADDRESSES column to see where the IP addresses are located in the Connectivity Diagram.