AFA administration
Relevant for: AFA Administrators
This topic lists supported browsers for working with ASMS, as well as a high-level instructions for using the AFA Administration area and setting up your AFA environment.
Note: For details about logging in or out of AFA, see Logins and other basics.
Access the AFA Administration area
Most AFA configurations are performed using the AFAAdministration area, accessible from the top-right of any AFA page.
Do the following:
In the toolbar, click your username, and then select Administration from the dropdown menu.
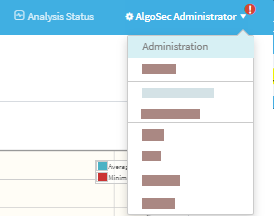
The Administration area includes the following tabs:
| DEVICES SETUP |
Manage devices, groups, and matrices. For details, see: |
| USERS/ROLES | Manage AFA users and user roles. For details, see AFA users and roles. |
| SCHEDULER | Schedule analysis and notifications. For details, see Schedule analysis. |
| COMPLIANCE | Manage risk profiles, baseline profiles, and compliance options. For details, see Customize risk and compliance management. |
| OPTIONS |
Configure AFA preferences including report storage options, user authentication options, backup options, and more. For details, see Define AFA preferences. |
| MONITORING | Configure real-time monitoring. For details, see Configure real-time monitoring. |
| INTEGRATIONS | Configure AlgoBot. For details, see Welcome to AlgoBot. |
| ARCHITECTURE | Manage Remote Agents or Load Units in a distributed architecture. |
Quickstart – Configure AFA to analyze devices
This section quickly introduces you to a few typical Administrative tasks and gets you analyzing devices in minutes.
Do the following:
- Collect your device policy automatically. Add devices for which you want to activate data collection. For more details, see Manage devices.
-
Configure AFA to run a nightly analysis. Once you have defined your devices for automatic data collection, you can schedule periodic analyses overnight, or at any other schedule of your choice.
For more details, see Schedule analysis.
-
Configure email notifications. AFA can send a variety of e-mail messages to you and to your team members when reports are ready or when changes are made on the monitored security devices. Additionally, you can schedule e-mails which contain dashboards.
For more details, see Configure notifications.
-
Manage user access.The AFA Web GUI allows you to view your reports on a secure web server, and lets you provide access to the reports to authorized team members.
Standard or Read-Only access can be granted to each user for each device separately. The Web GUI also allows authorized users to start analyses, to customize the resulting reports, and to run traffic simulation queries on them. AFA administrators may also use the Web GUI for administrative configurations.
For more details, see AFA users and roles.
â See also: