Additional FireFlow parameters
This section describes how to perform various FireFlow options using FireFlow configuration parameters.
Configure how long AFA data is stored in FireFlow cache
Note: Any configuration with the obsolete configuration parameter, FirewallObjectRefreshTime, needs to be reconfigured.
| Configuration Parameter Name | Value |
|---|---|
| FAServerCmdCacheLifeTimeInSeconds |
A copy of the default or current configuration, with the times modified as desired. The times are configured in seconds . See the example below for details. The default configuration for is as follows: { "CHECK_IF_DOMAINS_USED": 86400, "CHECK_REPORTS_BRANDS": 600, "FIREFLOW_APPLICATIONS_LIST": 86400, "FIREFLOW_FIND_LAST_REPORT_INFORMATION": 600, "FIREFLOW_FIND_LAST_REPORT_NAME": 600, "FIREFLOW_GET_GENERIC_DEVICES_BRAND": 86400, "FIREFLOW_GET_HOSTGROUPS_DEFINITION": 1200, "FIREFLOW_GET_MULTIPLE_PROTOCOL_SERVICES": 86400, "FIREFLOW_GET_SERVICE_OBJECTS_DEFINITION": 1200 } Example: The following value configures the amount of time that the device objects listis stored in cache to 3 minutes (180 seconds). The change appears in bold. { "CHECK_IF_DOMAINS_USED": 86400, "CHECK_REPORTS_BRANDS": 600, "FIREFLOW_APPLICATIONS_LIST": 86400, "FIREFLOW_FIND_LAST_REPORT_INFORMATION": 600, "FIREFLOW_FIND_LAST_REPORT_NAME": 600, "FIREFLOW_GET_GENERIC_DEVICES_BRAND": 86400, "FIREFLOW_GET_HOSTGROUPS_DEFINITION": 180, "FIREFLOW_GET_MULTIPLE_PROTOCOL_SERVICES": 86400, "FIREFLOW_GET_SERVICE_OBJECTS_DEFINITION": 1200 } Note: For further information regarding the various time values listed above and best practices for modifying them, contact AlgoSec. |
Configure queries on Juniper NSM devices to run on saved policies
By default, AFA runs all queries on the policy installed on the Netscreen device. If desired, you can configure queries to be run on the policy saved on the NSM. This enables you to validate a change was made correctly after implementing it on the NSM, but before installing it on the Netscreen device.
This configuration affects all queries in AFA. For FireFlow, this affects initial planning, work order creation, and change validation.
Note: Only new queries are executed against the saved policy. In order to query the new AFA saved policy for existing queries, re-execute the initial plans, work orders, and validations.
| Configuration Parameter Name | Value |
|---|---|
|
run_collect_nsm_upon_policy_save |
yes. To configure queries on NSM managed devices to run on the saved policy. |
Configure FireFlow to skip validation for suggested address objects
If desired, you can improve restart performance by bypassing the validation of the structure and consistency of the SuggestedAddressObjects_Config.xml file.
Although it is recommended to validate the consistency of the SuggestedAddressObjects file, in extreme cases where this file is significantly large, you may consider skipping the validation.
| Configuration Parameter Name | Value |
|---|---|
| SkipSuggestedAddressObjectsSchemeValidation |
0. To enable validation of the SuggestedAddressObjects_Config.xml file. (Default) 1. To skip validation of the SuggestedAddressObjects_Config.xml file. |
Customize the landing page
After logging into the AlgoSec Security Management Suite Firewall Analyzer or FireFlow will appear. See below for the default landing page for each user. For administrators, privileged users, and roles, you can override the default behavior by defining a landing page per user/role. For unprivileged users (requestors), you can override the default behavior by defining a landing page for all unprivileged users.
The landing page appears, according to the following precedence:
-
If a landing page is defined for the user, that landing page will appear.
-
If no landing page is defined for the user, but a landing page is defined for one of the user's roles, that landing page will appear.
-
If no landing page is defined for the user, and the user has multiple roles with different landing pages defined, the landing page is defined as FireFlow, and then AFA.
-
If no landing page is defined for the user or any of the user's roles, the following occurs:
For administrators AlgoSec Firewall Analyzer appears. For privileged (AFA) users The following occurs:
-
If FireFlow is licensed and activated, FireFlow appears.
-
Otherwise, the default AlgoSec Firewall Analyzer page appears.
For unprivileged users (requestors) The default FireFlow page appears.
-
Note: Only administrators and privileged (AFA) users can define landing pages. Administrators can define landing pages for themselves and others, while privileged users can only define landing pages for themselves. The procedures listed below can only be performed by administrators.
- Switch to AFA. For details, see Logins and other basics.
-
In the toolbar, click your username.
-
A drop-down menu appears.
-
Select Administration.
The Administration page appears displaying the Options tab.
-
Click the Users/Roles tab.
The User and Role Management page appears.
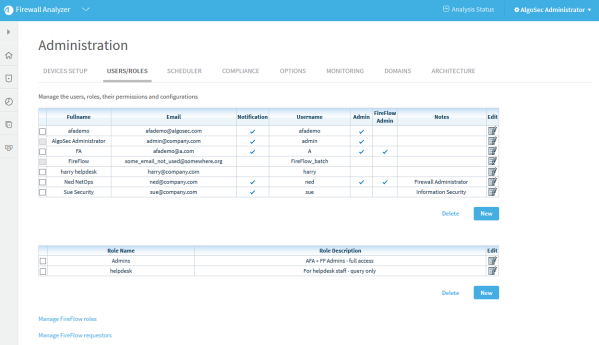
-
Click
 in the row of the desired user or role.
in the row of the desired user or role.New fields appear.
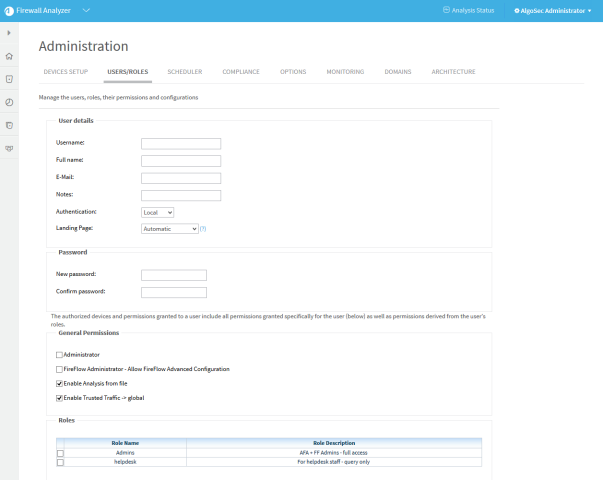
-
In the User or Role details area, in the Landing page drop-down menu, select the desired landing page.
-
Click OK.
- Switch to AFA. For details, see Logins and other basics.
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
The Administration page appears displaying the Options tab.
-
Click the Advanced Configuration sub-tab.
The Advanced Configuration sub-tab appears.
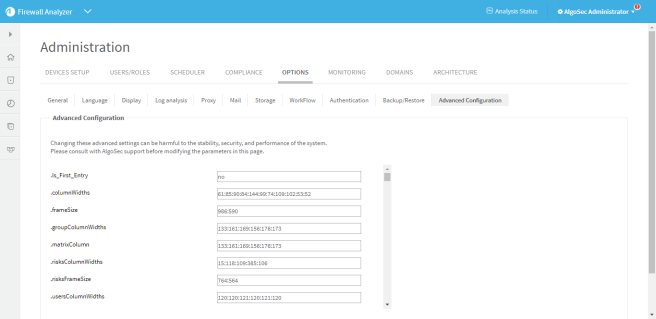
-
Click Add.
The Add New Configuration Parameter dialog is displayed.
-
In the Name field, enter FireFlow_Requestors_Landing_Page.
-
In the Value field, enter aff. This sets the landing page for all unprivileged users to FireFlow.
-
Click OK.
Configure the maximum number of rules in a rule removal request
By default, 50 is the maximum number of rules you can add to a rule removal change request. If desired you can change this.
To configure the maximum number of rules in a rule removal request
- Switch to AFA. For details, see Logins and other basics.
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
The Administration page appears displaying the Options tab.
-
Click the Advanced Configuration sub-tab.
The Advanced Configuration sub-tab appears.

-
Click Add.
The Add New Configuration Parameter dialog is displayed.

-
In the Name field, type Rule_Selection_Limit.
-
In the Value field, type the maximum number of rules.
Note: The maximum recommended value is 300. More rules than this in a single change request will severly impact performance.
-
Click OK.
Configure automatic approval of minor rule changes
By default, FireFlow displays any device policy rule changes in the Auto Matching page and attempts to match them to resolved change requests. This includes minor policy rule changes, such as enabling rule logging or updating a rule name. You can optionally configure FireFlow to automatically approve minor policy rule changes. These minor changes will then appear in the Auto Matching page in the Changes Without Request - Approved sub-list, without referring to a specific change request.
| Configuration Parameter Name | Value |
|---|---|
| IgnoreRuleFieldsInReconciliation |
A space-separated list of device policy rule fields, for which changes should be automatically approved. The supported policy rule fields are as follows: FirewallName, FirewallRuleNum, Name, Comment, Source, Destination, Service, SourceExpanded, DestinationExpanded, ServiceExpanded, Action, Enable, Track, Time, Install, Vpn, FromZone, ToZone, ACL, Interface, SourceNat, and DestinationNat. Note: SourceExpanded, DestinationExpanded, and ServiceExpanded are the IP addresses (and protocol/ports) represented by the rule’s object names. Therefore, for example, when adding Source to the value, changes in a rule’s source object names will be approved automatically, while changes to the actual source IP addresses will not. [] (an empty list). To specify that no changes should be automatically approved. For example, the following value configures FireFlow to automatically approve changes to rules that involve logging and/or comments only: [Track Comment] |
Customize the FireFlow risk check
The FireFlow default traffic change request lifecycle includes the Approve stage, in which a risk check is performed to determine whether implementing the change specified in a change request would introduce risks. The risk check is based on device analyses produced by AlgoSec Firewall Analyzer (AFA), a comprehensive device analysis solution that is a companion product of FireFlow.
It is possible to customize the FireFlow risk check, by configuring AFA to treat certain types of traffic as non-threatening trusted traffic when it produces the devices analyses. This enables you to eliminate false-alarms triggered by traffic that is necessary for the organization. In addition, you can create Risk Profiles that specify the severity level of individual risks. FireFlow risk check will then use your custom Risk Profiles to detect risks of your preferred risk level classification.
For more details, see Customize risk and compliance management.
Configuring Zero Touch for the multi-device object change workflow
By default, several stages in the multi-device object change workflow require user actions. The parameters that enable zero touch capabilities enable you to automate these stages:
| Parameter | Description | Workflow Stage | Values |
ObjectMultiDeviceWorkFlowSkipApproval
|
Controls skip approval behavior in the multi-device object workflow. | Approval |
0 - never skip to next stage (default) 1 - skip to next stage only if there are no affected rules 2 - always skip to next stage |
ObjectMultiDeviceWorkFlowImplementAutomatically
|
Controls implementation behavior on a device in the multi-device object workflow. | Implement |
0 - never implement automatically (default) 1 - always implement automatically |
For more details, see Multi-device object change workflow.