Do security changes take days or even weeks to process? Are you being bombarded with requests for connectivity changes for new business applications? Are misconfigurations causing costly business outages or creating dangerous holes in your security perimeter?
Many Security professionals struggle with manual security changes processes as they sift through hundreds and often thousands of firewall rules and access lists. The result: slow response to business requests, and costly mistakes that cause outages and introduce risk.
This technical webinar will provide best practices and tips to help you eliminate the risks of network security policy changes. You’ll learn:

AlgoSec Corporate Overview
An overview of AlgoSec's vision, solution, customers, partners, corporate values and achievements.
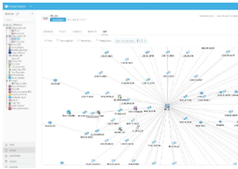
AlgoSec Firewall Analyzer- See the whole picture
Discover, identify, and map business applications and security policies – anywhere. With the industry’s app-centric perspective, you can now gain clear visibility into the security policies and the business applications that run your business — across your hybrid network. AlgoSec Firewall Analyzer enables you to stay on top of your security posture with continuous analysis and detection of risk and compliance gaps, allowing you to adapt quickly before an attack happens.
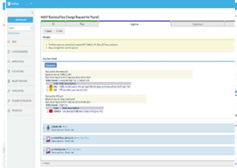
AlgoSec FireFlow - Automate and secure policy changes