FAQ about NIST Cybersecurity Standards
Understanding NIST Cybersecurity Standards is a crucial part of your network security compliance posture.
What are some common regulations that customers must be compliance with?
Do the NIST Cybersecurity Standards provide a checklist of what all organization should do?
No. The framework provides guidance that should be customized by different organizations to best suit their unique risks, situations, and needs. Organizations have different risks, threats, vulnerabilities, and risk tolerance. They will also differ in how they implement the practices in the framework. It should not be implemented as an un-customized checklist or take a one-size-fits-all approach
How does my firewall management help with NIST Standards and the NIST Cybersecurity Framework? What NIST standards relate to firewall management?
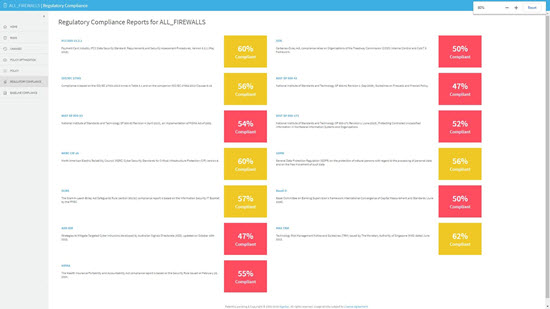
NIST Special Publication 800-41 establishes guidelines for firewalls and firewall policies, which govern standards and best practices for firewall policy management. According to the guidelines, an organization’s firewall policies should be based on a comprehensive risk-assessment. Firewall policies should be based on blocking all inbound and outbound traffic (“Default Deny”), with exceptions made for desired traffic. Policies should consider the source and destination of the traffic, in addition to the content. Many types of IPv4 traffic, such as those with invalid or private addresses, should be blocked by default. Organizations also should have policies for handling incoming and outgoing IPv6 traffic. Organizations should also determine which applications may send traffic into and out of its network and make firewall policies to block traffic for other applications. According to the guidelines (5.2.2), “if multiple firewalls need to have the same rules or a common subset of rules, those rules should be synchronized across the firewalls. This is usually done in a vendor-specific fashion.” AlgoSec provides out-of-the-box regulatory compliance reports for NIST SP 800-41.
What about NIST SP 800-53?
NIST SP 800-53, Security and Privacy Controls for Federal Information Systems and Organizations, relates to systems, including firewalls, that monitor and control at the external boundaries of the network and systems that connect to parts of the network. It provides extensive standards for firewall management. AlgoSec provides out-of-the-box regulatory compliance reports for NIST SP 800-53.
Do NIST standards also relate to FISMA compliance?
FISMA sets out guidelines for managing information security that must be followed for all information systems used or operated by a U.S. federal government agency in the executive or legislative branches, or by a contractor or other organization on behalf of a federal agency in those branches. By following NIST Cybersecurity Guidelines and NIST’s guidelines for firewalls and firewall policies, organizations get closer to FISMA compliance.
How AlgoSec Helps with NIST Standards?
AlgoSec helps identify traffic flows and associate it with the relevant business applications, and design firewall policies that work across your hybrid network, all with zero-touch automation to reduce the chances of manual misconfigurations. AlgoSec also helps manage and synchronize rules across the multi-vendor estate, so there is holistic and unified management across a network made up of multiple vendors. By using AlgoSec, organizations can be sure that their security management practices follow best practices such as NIST standards.
AlgoSec automatically generates pre-populated, audit-ready compliance reports for leading industry regulations, including NIST SP 800-53, NIST SP 800-41, SOX, GLBA, PCI DSS, and ISO 27001— which helps reduce audit preparation efforts and costs. AlgoSec also uncovers gaps in organization’s compliance posture and proactively checks every change for compliance violations. AlgoSec also provides daily audit and compliance reporting across the entire heterogeneous network estate.
Resources
See how AlgoSec can help you meet NIST Cybersecurity Standards. Check out these resources.


 Watch Webinar
Watch Webinar